NIST Cyber Defense Strategy
A cyber-attack is an existential threat to your organization. It’s no longer a question of “if” any given company or organization is going to be hit with a cyber-attack — it’s when.
Every company—large, small, in healthcare, technology, manufacturing, and more—has a cyber risk. And almost every day now, we learn about yet another cyber security incident. Be it ransomware, phishing emails, malware, or user data breach, companies are finding themselves the target of a cyber-attack all too often. Cybersecurity and privacy are urgent concerns for every organization, keeping sensitive data private, intellectual property proprietary, and critical business systems up and running can seem nearly impossible in the face of relentless and ever-sophisticated attacks and breach attempts.
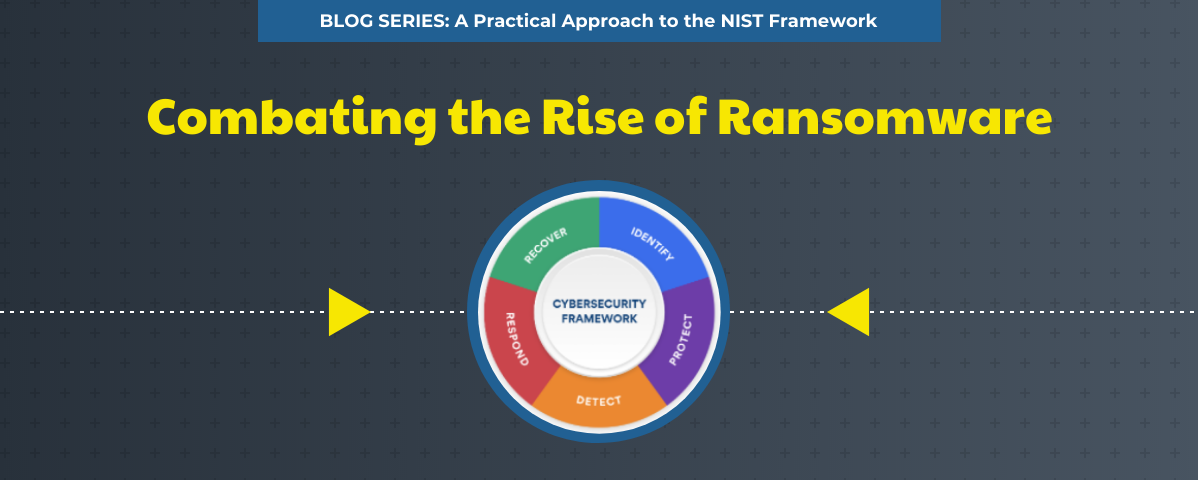
That’s why the National Institute of Standards and Technology (NIST) developed the Cybersecurity Framework (CSF). NIST’s goal was to establish a common set of standards, goals, and language to increase information security and better remediation of the fallout after a cyberattack. It enables organizations of all sizes to discuss, address, and manage cybersecurity risk. And without reinventing the cyber wheel, it references existing best practices through its Core functions.
Identify
The Identify Function assists in developing an organizational understanding to managing cybersecurity risk to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs.
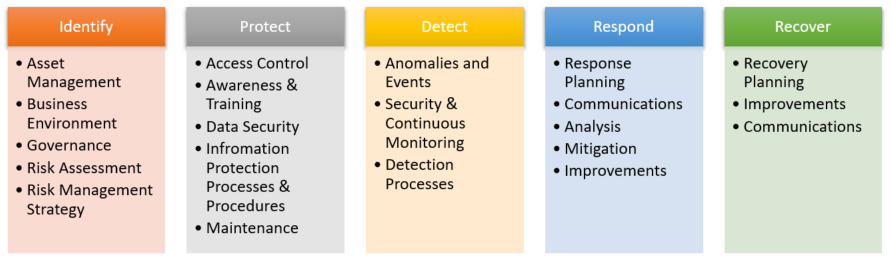
Examples of outcome Categories within this Function include:
- Identifying physical and software assets within the organization to establish the basis of an Asset Management program
- Identifying cybersecurity policies established within the organization to define the Governance program as well as identifying legal and regulatory requirements regarding the cybersecurity capabilities of the organization
- Identifying asset vulnerabilities, threats to internal and external organizational resources which can be done via dark web scan
- Identifying a Risk Management Strategy for the organization including establishing risk tolerances
- Identifying a Supply Chain Risk Management strategy including priorities, constraints, risk tolerances, and assumptions used to support risk decisions associated with managing supply chain risks
Protect
The Protect Function outlines appropriate safeguards to ensure delivery of critical infrastructure services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event.
Examples of outcome Categories within this Function include:
- Empowering staff within the organization through awareness and training and developing a cyber aware culture
- Establishing data security protection consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information
- Implementing information protection processes and procedures to maintain and manage the protections of information systems and assets
- Protecting organizational resources through maintenance, including remote maintenance, activities
- Managing protective technology to ensure the security and resilience of systems and assets are consistent with organizational policies, procedures, and agreement
Detect
The Detect Function defines the appropriate activities to identify the occurrence of a cybersecurity event. The detect function enables timely discovery of cybersecurity events.
Examples of outcome Categories within this Function include:
- Ensuring anomalies and events are detected, and their potential impact is understood
- Implementing security continuous monitoring capabilities to monitor cybersecurity events and verify the effectiveness of protective measures including network and physical activities
- Maintaining Detection Processes to provide awareness of anomalous events
Respond
The Respond Function includes appropriate activities to take action regarding a detected cybersecurity incident. The Respond Function supports the ability to contain the impact of a potential cybersecurity incident.
Examples of outcome Categories within this Function include:
- Ensuring Incident Response Planning processes are executed during and after an incident
- Managing Communications during and after an event with stakeholders, law enforcement, external stakeholders as appropriate
- Analysis is conducted to ensure effective response and support recovery activities including forensic analysis, and determining the impact of incidents
- Mitigation activities are performed to prevent expansion of an event and to resolve the incident
- The organization implements Improvements by incorporating lessons learned from current and previous detection / response activities
Recover
The Recover Function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident.
Examples of outcome Categories within this Function include:
- Ensuring the organization implements Recovery Planning processes and procedures to restore systems and/or assets affected by cybersecurity incidents
- Implementing Improvements based on lessons learned and reviews of existing strategies
- Internal and external communications are coordinated during and following the recovery from a cybersecurity incident
Curious if NIST is the right security framework for your business? Take our cybersecurity framework assessment.
Even with the NIST Cybersecurity Framework, many organizations still need more help. Critical tasks like risk assessment, gap analysis, action planning and constantly changing security solutions are left to IT teams. At Next Dimension, we can help you fight evolving cyber threats with best-in-class security solutions and take the stress off your teams. Our managed services provide your business with end-to-end security monitoring, threat detection, and incident response. Let us take care of your security while you focus on your business.